At times, you might need to limit access to your S3 bucket to only a particular resource. Although there are various methods to grant permission via S3 bucket policy, the simplest and most frequently used approach involves permitting access based on the resource’s role ARN, utilizing the condition key named aws:PrincipalArn.
目次
Example Scenario
Consider a scenario where there are three EC2 instances: EC2 A, EC2 B, and EC2 C. Your objective is to exclusively permit access to the S3 bucket named “esar-bucket” solely for EC2 A. In this setup, EC2 A possesses its role and IAM permissions, enabling it to access the specified bucket while restricting EC2 B and EC2 C from gaining entry to the same bucket.
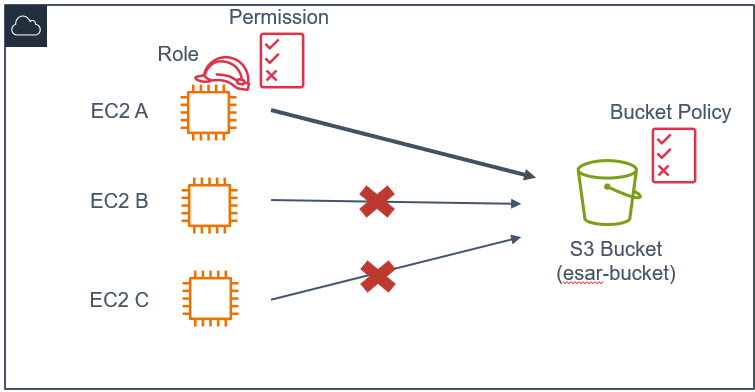
The Wrong Way
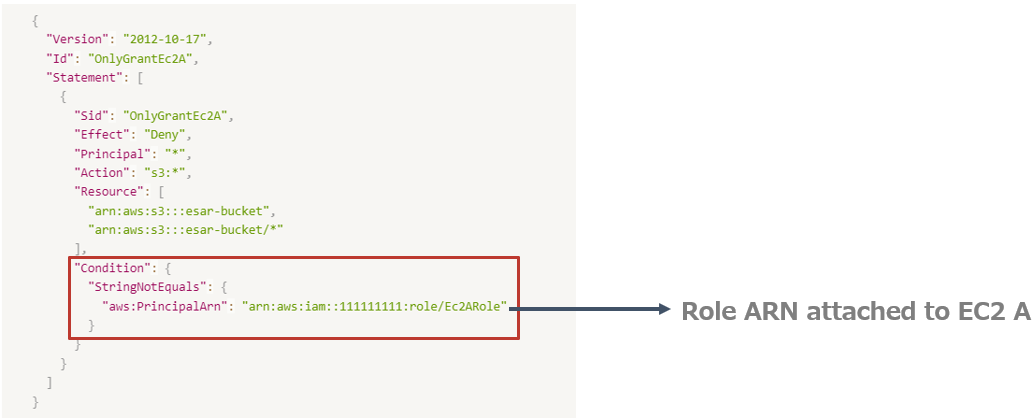
To ensure exclusive access for EC2 A, you can include EC2 A’s role ARN within the bucket policy.
Here’s an example structure of how the bucket policy could be formulated:
Let’s review our S3 bucket using the AWS console.
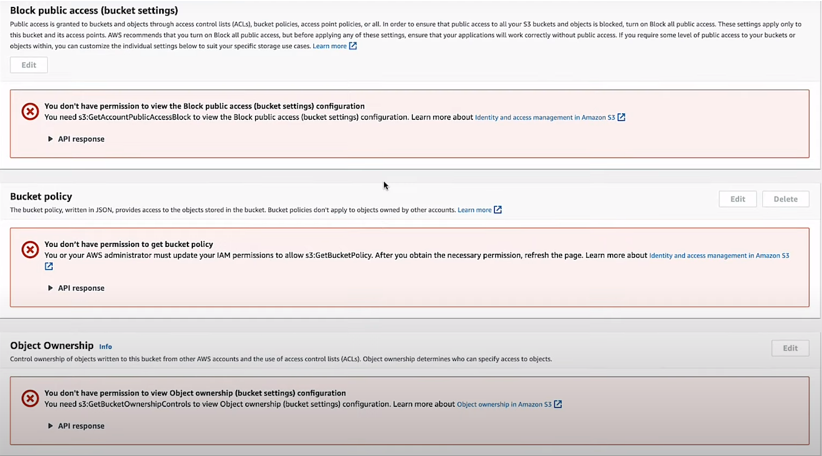
Great work! Congratulations, the bucket is now inaccessible to everyone, including yourself. You’re currently locked out of your own S3 Bucket.
At this point, only EC2 A can indeed access the bucket, but we won’t be able to modify or view the bucket policy. So, this approach is rather pointless.
The Correct Way
Although solutions may vary, the following approach stands out as one of the simplest methods.
Consider a scenario where you access your AWS console using your company’s static IP address as an example.
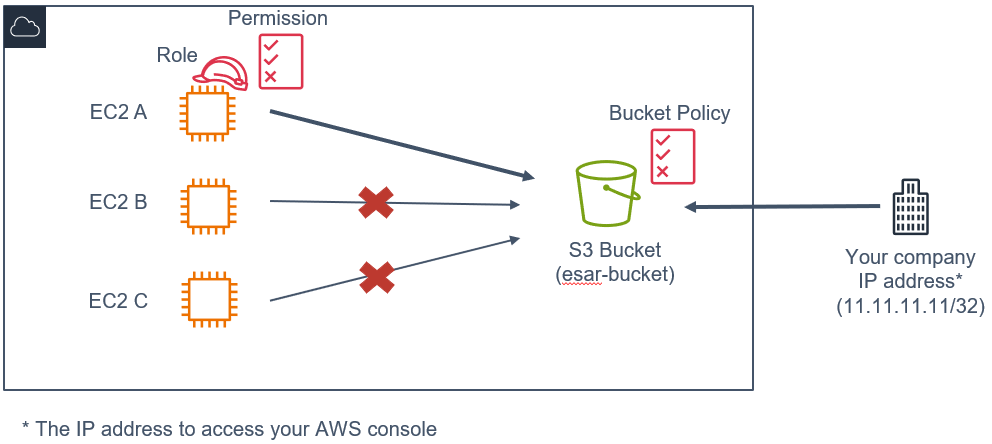
To avoid the risk of getting locked out of the S3 bucket, we can include the company’s IP address in the bucket policy within the condition statement.
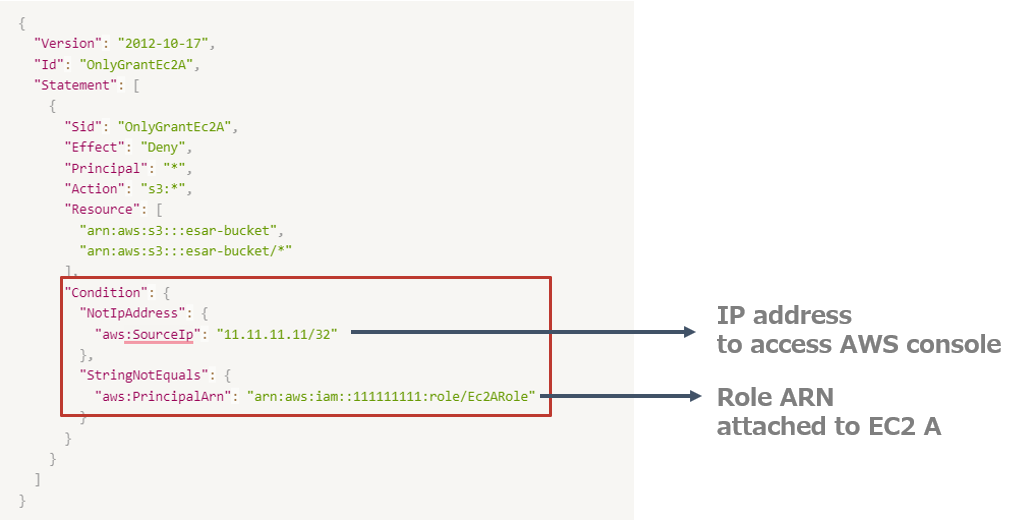
Conclusion
In conclusion, configuring a bucket policy is a straightforward process. Yet, an incorrect configuration might render the bucket inaccessible via the AWS Management Console, or worse, lead to being locked out of the S3 bucket.
Feel free to customize and adjust this approach to suit your specific scenario and requirements.
- 【React】フロントエンドのテストコードを書いてみよう【Vitest】 - 2024-04-30
- Simple AWS DeepRacer Reward Function Using Waypoints - 2023-12-19
- Restrict S3 Bucket Access from Specified Resource - 2023-12-16
- Expand Amazon EBS Volume on EC2 Instance without Downtime - 2023-09-28
- Monitor OpenSearch Status On EC2 with CloudWatch Alarm - 2023-07-02
【採用情報】一緒に働く仲間を募集しています